Latest Posts
Just recently, numerous users have reported seeing the Mistake Code: DLG_FLAGS_INVALID_CA on their Chrome web…
Do you want to know which is the best NES emulator for PC in 2023? No…
Are you looking for the best place to buy sports tickets? Want to find discount…
If you’re considering investing in silver, buying online can offer convenience and a wide range…
Who doesn’t love watching movies? Movies are said to be the most popular and favorite…
Are you a movies fan? Do you like streaming and downloading movies on the Viooz…
Visitors of the site streamsnooper.com can browse and download live streams and video materials. The…
Here are multiple communication channels over the internet, and ChatStep is one of them. It’s…
This post will explain 3D Slash software alternatives. 3D Slash has simple-to-use 3D modeling tools,…
This post will explain nhl66 alternatives. NHL66 is the official web site of the National…
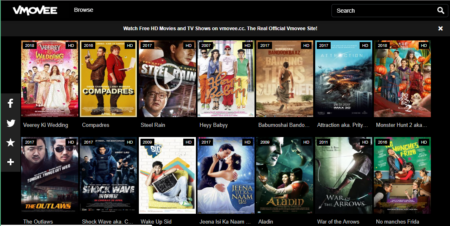
This post will explain Vmovee. Not an age-old site utilized for streaming films online however…
This article explains the Websites to replace desktop software. When you have a web browser,…
More Updates
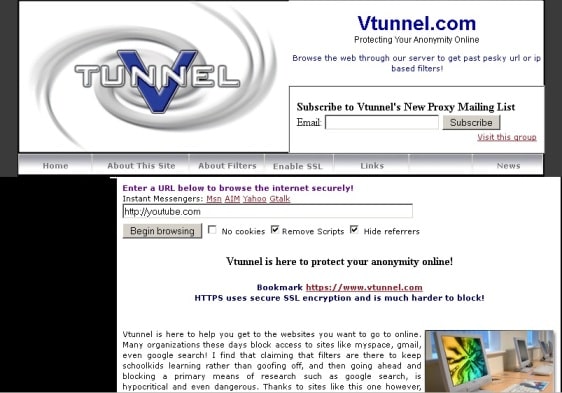
Vtunnel is one of the most famous and successful proxy…
Popular posts:
- 21 Best MangaReader Alternatives Read Manga Online Free
- Top 10 Viooz Alternatives Sites Updated for 2024
- 27 Best Manga Raw Alternatives Read Manga Online Free
- 26 Best ComicWalker Alternatives Read Manga Online Free
- 27 Best Hiperdex Alternatives Read Manga Online Free
- Top 10 Alternatives of Pandamovies Free Streaming in 2021
- MamaHD Alternatives 25 Best Sites To Watch Sports Online
- The 10 Best Totalsportek Alternatives For Live…
- Streamsnooper Alternatives 10 Best Sites To Stream…
- Top 10 Best Fmovies Alternative Sites Updated For 2024






![[Solved]: DLG_FLAGS_INVALID_CA error In Google Chrome DLG_FLAGS_INVALID_CA Google Chrome](https://gokicker.net/wp-content/uploads/2021/06/your_connection-450x335.jpg)